Web3 Compliance Research | 2025 New Aiding-and-Abetting Rules — What Do They Mean for Web3 Practitioners?
In 2015, China’s Criminal Law introduced the offense of “Assisting Information Network Criminal Activities” (commonly referred to as “Aiding IT Crimes”). As the crackdown on financial crime intensified through the “Card Severance” campaign, prosecutions for this crime have skyrocketed—it now ranks third among all criminal cases in China, based on public data. The offense provokes mixed reactions: on one hand, it’s considered “preferable” by some because liability is lighter than for co-perpetrators; on the other, it’s a challenging fallback provision, making it hard to avoid serious legal consequences. In practice, interpretation and sentencing standards for this crime vary widely among local courts, resulting in inconsistent rulings across similar cases. On July 28, 2025, the Supreme People’s Court, Supreme People’s Procuratorate, and Ministry of Public Security jointly issued the “Opinions on Handling Criminal Cases Involving Assisting Information Network Criminal Activities” (“the Opinions”), which serve as an authoritative new regulatory framework for this offense—often called the “New Aiding IT Crimes Regulation.”
What’s New in the Aiding IT Crimes Regulation?
The Opinions fundamentally revise the standards for establishing and sentencing the crime of aiding IT crimes. The main changes include:
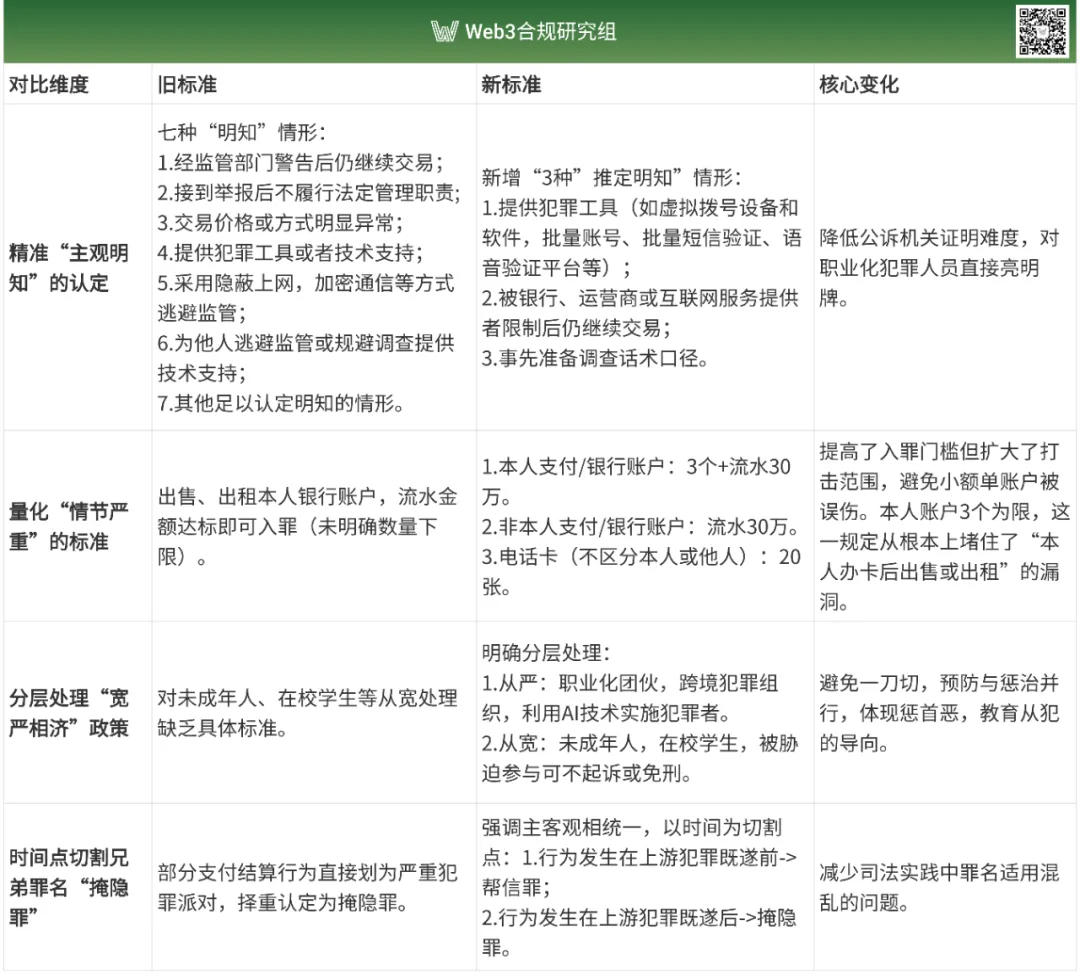
What Judicial Guidance Do the Seven Typical Cases Offer?
When the Opinions were released, authorities simultaneously published seven representative cases, covering critical roles within the “black and gray” cybercrime market—including “U merchants,” “account merchants,” and “professional unblocking service providers.” Notably, Case 4 centers on crimes involving virtual currencies. A detailed look at both the Opinions and these cases reveals little procedural difference from standard criminal cases, but the enforcement measures against network crimes and cybercrime supply chains are both stricter and more forceful.
[Case Summary] In mid-July 2022, defendants Wang, Zhang, and Zhao conspired to profit illegally by helping others move criminal proceeds via bank transfers, cash withdrawals, and virtual currency conversions. Their roles were clearly defined: Wang supplied funds, Zhao used those funds to purchase virtual currencies and transferred them to their higher-up as a deposit, while Wang and Zhang acquired large numbers of bank cards and supplied them to the ringleader for use in receiving illicit funds. Once the criminal proceeds were deposited into these cards, their superior would instruct them to have others withdraw cash from multiple banks in Daqing City, Heilongjiang Province. After deducting a 10%-15% commission from the withdrawn funds, the remainder was used to purchase virtual currency and sent to the ringleader. An investigation found that from August 5 to August 14, 2022, Wang and his associates transferred more than RMB 400,000 in fraud proceeds belonging to 15 victims including Lin.
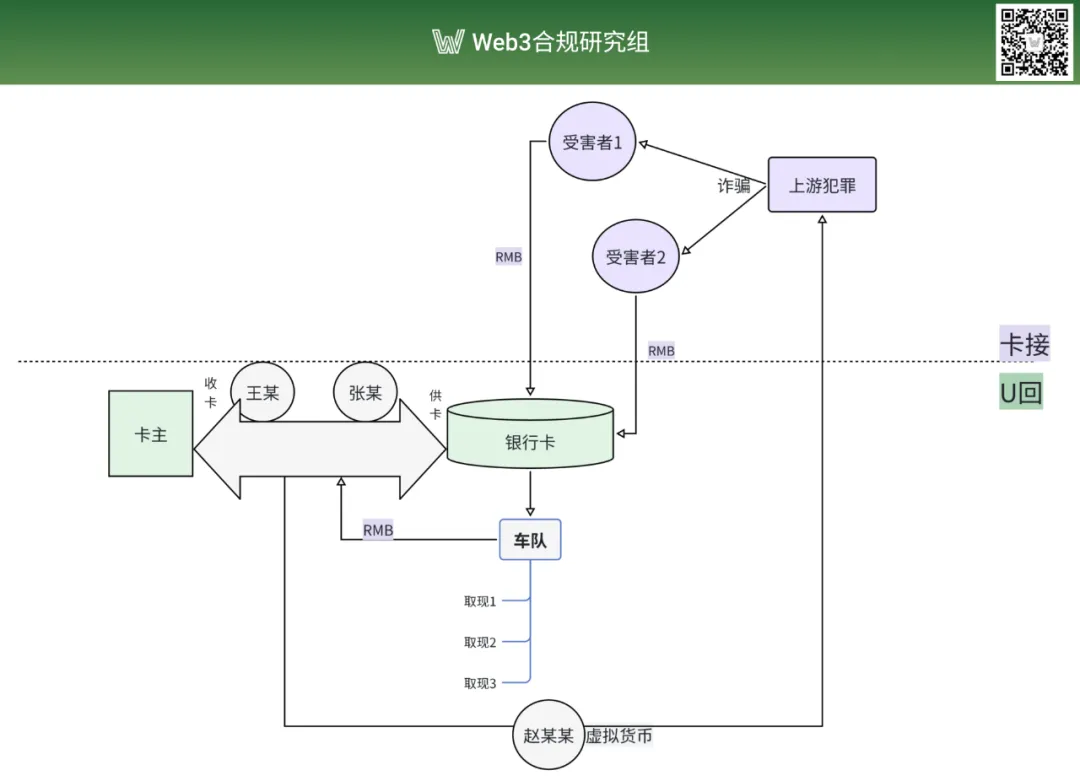
[Court Decision] The Acheng District People’s Court in Harbin found Wang and Zhang guilty of concealing and disguising criminal proceeds, sentencing each to three years and six months in prison plus a RMB 30,000 fine; Zhao received three years and three months in prison and a RMB 25,000 fine. All three appealed, but the appeals court upheld the original judgment.
[Legal Warning] Wang, Zhang, and Zhao laundered illicit proceeds by exchanging criminal funds received through bank cards into virtual currency, providing a textbook example of using the “Card-to-U and Back” method to move illegal funds through crypto transactions—a process many criminals view as the perfect “closed loop.” In practice, upstream fraudsters—often located overseas—exploit crypto’s anonymity, high concealment, and convenience to move stolen funds and obstruct law enforcement investigations. Downstream accomplices facilitate the laundering and transfer, fueling upstream crimes and ultimately causing severe, often irreparable losses for victims. This case not only illustrates the specific application of the Opinions but also provides clear behavioral guidance and legal standards: even intermediaries who simply facilitate illicit fund flows should be held strictly accountable, whether or not they were directly involved in upstream fraud.
What Should Web3 Professionals Watch For Under the New Regulation?
For Web3, growth is possible only “if compliance comes first.”
1. The new regulation delivers a clear signal: ignorance is no longer a blanket shield. Web3 professionals must prioritize legal literacy, remain vigilant, implement robust risk controls, and establish strong compliance strategies to ensure lawful operations. Failing to do so could turn one into a tool or accomplice for criminals—even unknowingly.
2. With a balanced policy of leniency and severity, students or those coerced may receive lighter treatment, while technical experts face heightened penalties. After the Opinions were issued, engineers and operators of virtual currency exchanges, mixers, and anonymous wallet technologies need to be especially alert: even without direct participation in fraud or pyramid schemes, developing solutions that enable illegal activity can itself constitute aiding IT crimes. This shifts the standard from “technical neutrality” to “technical assistance.”
3. OTC merchants are “playing with fire”—criminal liability risks have increased sharply. If an OTC merchant continues trading after an account freeze, authorities may charge “continuing activity after restriction,” directly constituting aiding IT crimes. Providing USDT matching services to underground money brokers could bring multiple charges.
4. Compliance is now non-negotiable for Web3 startups. Founders should establish industry-specific compliance systems as soon as possible and provide regular legal training for all team members.
From a Lawyer’s Perspective: Key Impacts and Challenges of the Opinions
The Opinions set stricter punishment guidelines for organized and professional aiding behaviors. This not only raises the cost for upstream perpetrators but also enables tough enforcement against professional card providers and similar bad actors. While the Opinions clarify conviction and sentencing standards—offering lawyers clearer rules and legal grounds for defense—the criterion for “knowing participation” remains ambiguous in complicated cases. Factors like subjective awareness, motivation, and financial incentives require thorough investigation. In short, the release of “Opinions on Handling Criminal Cases Involving Assisting Information Network Criminal Activities” signals a new era of “penetrative” regulatory enforcement over the crypto sector in China. Industry participants must realize that only a comprehensive compliance system spanning pre-event review, in-process monitoring, and post-event tracing will allow legal business operations.
Attorney Meimei recommends crypto industry practitioners avoid activities that could constitute “aiding” crimes—even inadvertently—and seek immediate legal counsel if investigated to prevent statements being interpreted as willful involvement.
Disclaimer:
- This article is reprinted from the [Web3 Compliance Research Group]; copyright belongs to the original author ([Attorney Pang Meimei]). For any concerns about republication, please contact the Gate Learn Team for prompt handling in accordance with relevant procedures.
- Disclaimer: The views and opinions expressed herein represent only the author’s personal perspectives and do not constitute investment advice.
- Other language versions are translated by Gate Learn and may not be copied, distributed, or plagiarized without referring to Gate.
Related Articles

Solana Need L2s And Appchains?

The Future of Cross-Chain Bridges: Full-Chain Interoperability Becomes Inevitable, Liquidity Bridges Will Decline

Sui: How are users leveraging its speed, security, & scalability?

Navigating the Zero Knowledge Landscape

What is Tronscan and How Can You Use it in 2025?
